The conventional frameworks of identity management have always concentrated on managing the users of the organisation and granting them access and privileges to the organisation's assets.

They have primarily supported techniques in predictable on-premises work environments. Today’s multichannel, multi-device and mobile-enabled environment demands more ways to engage as well as transact with businesses and their digital services.
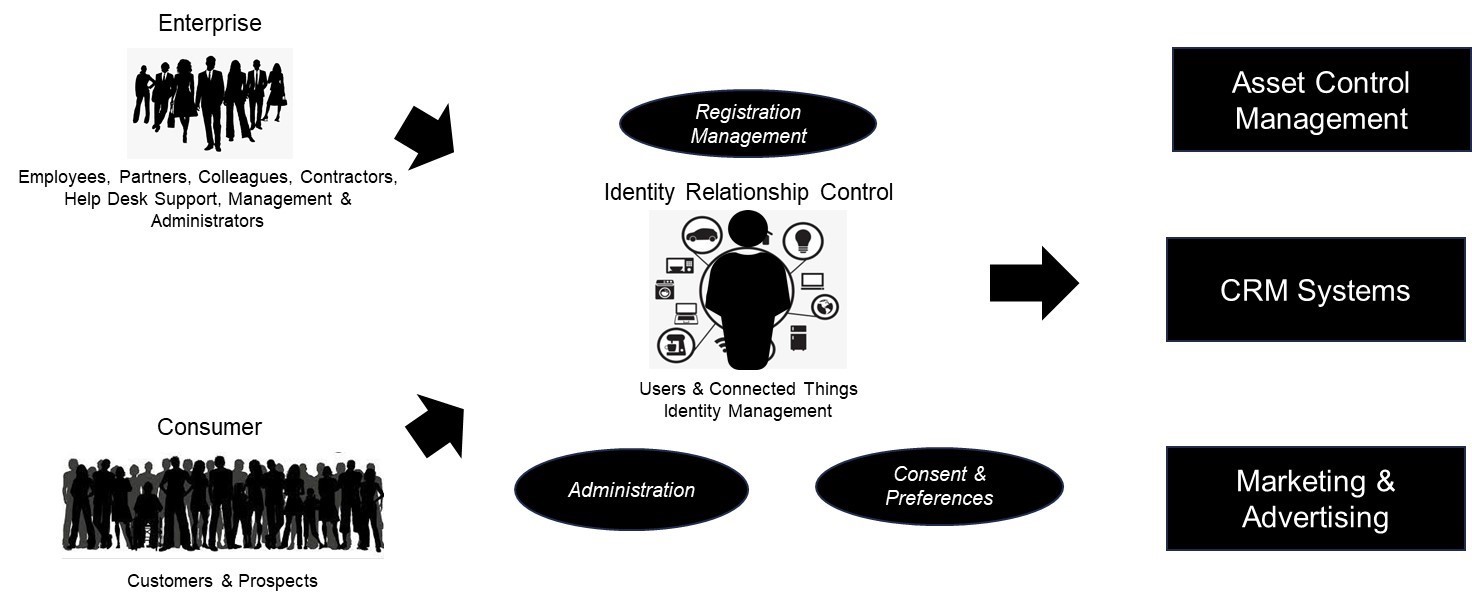
Users expect to deepen the connections on their own terms, at any time from anywhere on any device they choose. Identity relationship control is the next generation of identity management where it links people, places, and things and enables a dynamic, context-based strategy that organisations and businesses can apply throughout the lifecycle management of users (enterprise and customers both).
Convergence and Evolution of Identity Management Solutions
Identity proofing, credential management and identity attributes management will still remain the core tenets or pillars of the registration services. The services in these areas are going digital rather than the physical presence of the individual, especially for Identity proofing. The elements that are changing are more in the areas of consent, preferences and administration. Privacy & data security regulations ensure users have more control and say in the information that is stored about them by organisations and businesses.
Consent and preferences include capabilities that allow users to control how their personal information is used by organisations and businesses. It further provides an ability for users to opt out at any point in time from sharing their information. Delegated administration is another feature expected by users in identity relationship management services where the users can delegate the controls to other users whom they trust to perform tasks and make decisions on their behalf for a finite amount of time. This may occur at any point of the life cycle management, and they should be able to take back control when the need is completed.
As market influences have evolved, consumers continue to demand higher levels of efficiency and services. Consumers regularly feel the need to always be in control of their information and how they want it to be shared through Identity Management solutions.
The lines are getting blurred between enterprise and consumer identity solutions. There will be always one unique identity of an individual human being but the relationship and context change based on the way the individual/consumer/user would like to control it through consent, preferences and delegated administration.
Self-service features have become increasingly popular and are also increasing, helping organisations and businesses to keep their costs down and spending for registration authority personnel, help desks and customer support capabilities.
To learn more, please reach out to our experts Denise Walker (denise.walker@mastek.com) and Rashi Malhotra (rashi.malhotra@mastek.com).

.png?width=100&height=100&name=MicrosoftTeams-image%20(16).png)