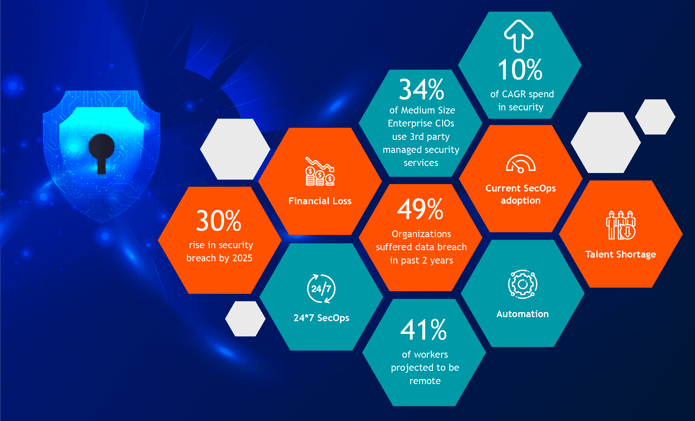
Impacts of changing landscape
- Two years into the deadly and disruptive global pandemic, not only are we continuing to see more attacks, but we’re also seeing more actual breaches which result in significant financial losses, reduction in getting new business, and losing trust with existing customers.
- In today's scenario, most organizations have adopted agile methods for software development which has shortened Go-To-Market by deploying changes quickly to the production environment. A security vulnerability leak could cause significant damage in no time and the cost of such an incident might outweigh the security budget
- Implementing security keeps getting harder with more threats, complexity, and fewer people and hence we see a lot more cyberattacks and breaches
- Top 3 attacks of 2021:
- SolarWinds attack had 18000 customers impacted
- REvil hit Apple supplier Quanta with a $50 million ransomware attack
- Apache Log4j, a zero-day vulnerability attempted to exploit more than 48% of corporate networks globally.
- 2022 so far:
- The war in Eastern Europe has triggered cyber warfare (criminal ransomware, hacktivists or other disruptive attacks against government or critical infrastructure) with potential disruptive activities and information operations to erode popular sentiment and political will.
- Major causes for vulnerabilities:
- Current trend as per Trend Micro:
- 80% of application code is open source
- 2.5x increase in open source vulnerabilities in the last 3 years
- 78% of vulnerabilities are found in in-direct dependencies
- As per Gartner, through 2023, at least 99% of cloud security failures will be the customer’s fault, mainly in the form of cloud resource misconfiguration.
- Current trend as per Trend Micro:
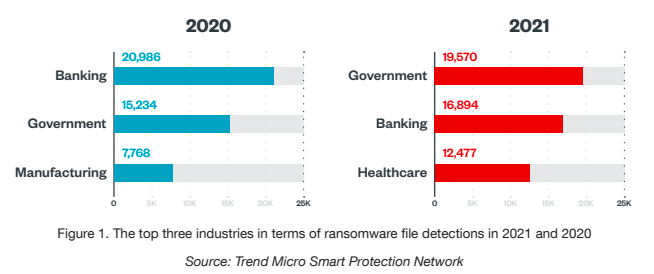
- A 2021 report suggests that because healthcare organizations are less likely to back up their data than those in other industries, they are more prone to paying the demands of ransomware actors. Please refer to Figure 1 for its trend.
Top drivers that determine security decisions for CISO
The following are the most common influencing factors that determine the decisions for application security:
- Customer Risks
- Regulatory compliance
- Security awareness in organizations (OWASP, SANS, etc.)
- Lessons learnt from past experience
- The approach to security makes our software more marketable
- Users tell us about vulnerabilities in our software
Elements of DevOps and its security concerns
The following diagram helps in understanding what various security concerns are in each stage of the DevOps lifecycle:
Figure 2
Mastek's SecOps Offering
We provide bespoke offerings for security as per customer needs in the following areas:
- Integrate security at each stage of DevOps
- IAST, SAST, and DAST to scan vulnerabilities
- Container security analysis & vulnerability management
- Threat modelling and Report generation
- Secure with native and cloud platform
- Prismo integration to existing DevOps estate
How is Mastek enhancing its footprint in security?
- To provide a seamless experience of DevSecOps implementation to customers, we are investing heavily in the area of security in terms of resources and capabilities.
- We are also spending considerable efforts in building DevSecOps accelerators with security incorporated at all stages of DevOps which can be leveraged by customers to rapidly onboard and secure their applications without any hassle.
- We have incorporated SecOps in Agile DevOps Ways of Working.
- We are partnering with industry-leading security providers like Prismo a niche player in the security space.

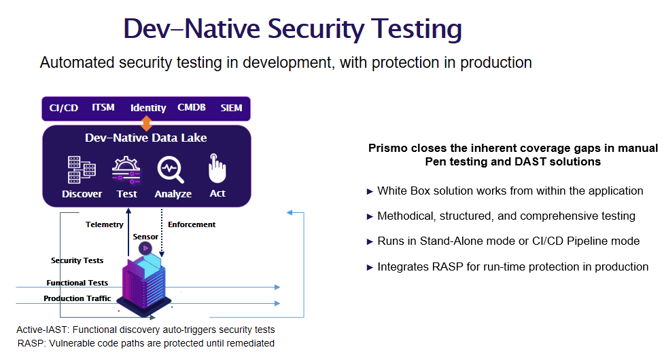
Figure 3
Mastek's approach to addressing security concerns
Figure 4
How is cloud-native security addressed?
Let’s think about security in layers for the cloud. The 4C's of Cloud Native security are Cloud, Clusters, Containers, and Code. This layered approach augments the defense in depth computing approach to security, which is widely regarded as a best practice for securing software systems.
- Cloud – It is the foundation of all security layers, and every cloud provider (like AWS, Microsoft Azure, Google Cloud, IBM Cloud) provides infrastructure security for the running workloads.
- Clusters – The primary security concerns in this layer are RBAC authorization, secrets management, pod security policies, and network policies, and Kubernetes is the standard operating tool.
- Containers – The security postures recommended in this layer are container vulnerability scanning, image signing, and creating users inside of the containers that have the least level of operating system privilege necessary.
- Code – Organizations have the most control over this layer and can implement security recommendations like performing static code analysis, adopting DevSecOps practices, and making security part of the CI/CD pipeline.
Shift Left security approach considerations
Shifting security left in the DevSecOps cycle dramatically improves quality by identifying and fixing security-related defects early in lifecycle, thereby reducing the cost of fixing security vulnerabilities at later stages.
- Input validation from UI
- Secure coding standards
- Data sanitization: input
- Deliberate architecture and design sessions on security
- Principle of least possible privilege
- Whitelisting (permission explicit, denial default)
- Static code analysis for security
- Simple design to shrink the attack surface
- Data sanitization: output
- Penetration testing
- Policy of not ignoring compiler warnings
- Threat modelling
- Defence in depth
- Fuzz testing
- Role-based/User training
How do security operations help?
Some of the benefits of implementing security ops are listed below:
- Automated vulnerability management and audit and compliance reporting reduce human effort, errors, and costs
- Automated mapping to NIST CSF and ZTA, MITRE ATT@ck, OWASP, and other standards provides a future-proof solution for evolving compliance requirements
- Significant reduction in cost of fixing vulnerability at a later stage
- Security ensured even with ever-changing attack patterns
- Win customer confidence and reputation with secured product
- Rapid response and recovery in the case of a security incident
Prismo Improves Key Metrics at Every Stage of the CI/CD
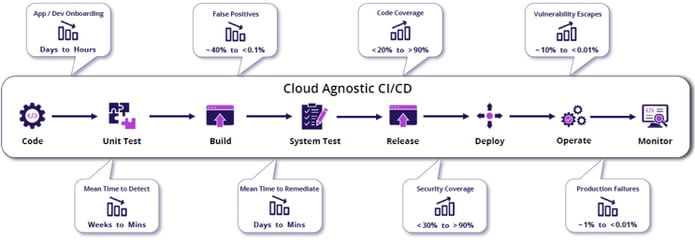
Figure 5